Two-factor authentication (2FA) and multi-factor authentication (MFA) have been around for quite some time. MFA is the broader term of the two. They consist of you having to input something else in conjunction with your password to log in. That is, you need two secrets to authenticate. Every time you need to add an additional password or code in addition to your password, it’s a form of MFA.
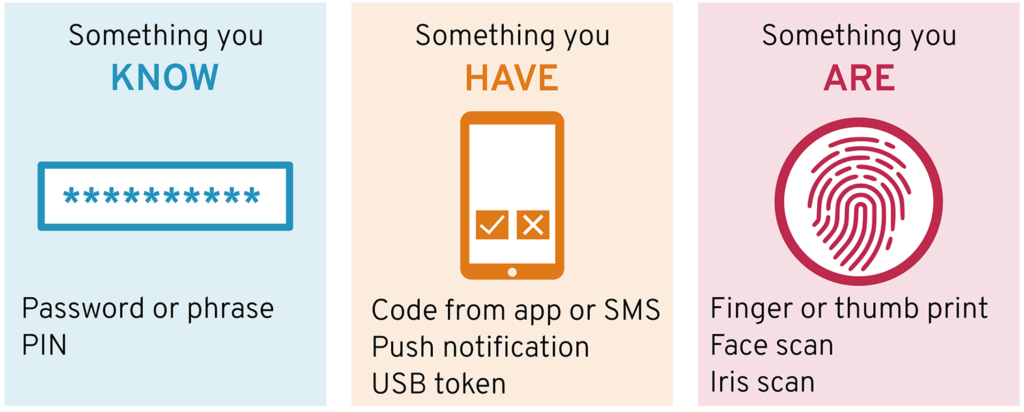
MFAs can be categorized into three categories:
- Something you know: Password
- Something you have: A smartphone
- Something you are: Biometric data, e.g., a fingerprint
One-time passwords (OTP) are codes, passwords, pins, or other temporary and unique codes that you input.
Sometimes these OTP can be SMS-based; you get a code sent to your phone when logging in to authenticate yourself. The problem with SMS-based MFA is that an SMS can be manipulated or easily intercepted by bad actors. So to log in, you need a username, password, and OTP to authenticate yourself.
Why do we do this? This is done to enhance the overall security to authenticate yourself. Due to the issue with passwords, passwords are easy to reuse, and people do so. So when we use MFA, we get a bit more security because the user cannot reuse the authentication input.
Most used passwords 2023:
- 123456
- 123456789
- qwerty
- password
- 12345
- qwerty123
- 1q2w3e
- 12345678
- 111111
- 1234567890
So we have issues with people reusing passwords and old, outdated, and not so secure MFA methods, like SMS-based ones. So the FIDO Alliance is meant to solve these issues by providing a more robust and secure way to provide MFA.
In the mainstream tech world, the two most important FIDO standards are FIDO U2F (Universal 2nd factor) and FIDO2, which is an extension of the FIDO U2F standard.
The U2F protocol involves physical keys, often USB keys used with a fingerprint sensor to additionally authenticate the user. So now the user needs: a username/email, password, a physical hardware key, and the user’s fingerprint. Now we have an MFA system where the user needs to provide something they know, have, and are. A popular U2F hardware key is the YubiKey.

The FIDO2 involves two components:
- WebAuthn: is used with web applications to let websites use FIDO2 devices to do authentication.
- Client to Authentication Protocol (CTAP): It is a protocol that lets FIDO2 devices and user devices (computers, smartphones, etc.) do secure authentication.
The issues with MFA are the need for additional steps to be performed by the user, so that might lead to users not implementing MFA. It also comes with additional implementations for developers and companies to add MFA to their products and services. But the positives are much greater than the negatives. I mean in this day and age we need stronger authentications. Passwords aren’t cutting it these days. A good internet user would need to use: a password manager, MFA, and good computer and internet hygiene. Passkeys are also something that has been brought up, and they might aid the authentication dilemma. I might write some about password managers, passkeys, and so on.
There are open-source free password managers and MFA applications. So the ease to implement isn’t difficult; one just needs to do it. So just do it! Our everyday life is online, and we need to protect ourselves. People often say that they have nothing to hide, so they don’t care. I often ask them, “Well, let me get your phone and home keys, and I can visit you whenever and go through all your files, messages, and kitchen cupboards without you intervening. Would you lend me your phone and house keys?”